Security Subsystem
With the recent progress of the IoT (Internet of Things), a security system has become an essential item. Although a high level of protection for secret information and high-speed algorithm processing by hardware are indispensable for a security system, it is not easy to develop such hardware and software from scratch. Using Socionext's security subsystem can reduce the burden of such development, making it possible for you to introduce a security system efficiently.
Outline
The security subsystem includes a dedicated key storage box to store highly secret key information. It also incorporates a hardware engine that uses the stored key to perform high-speed encryption and authentication processing, achieving a high-level security system.
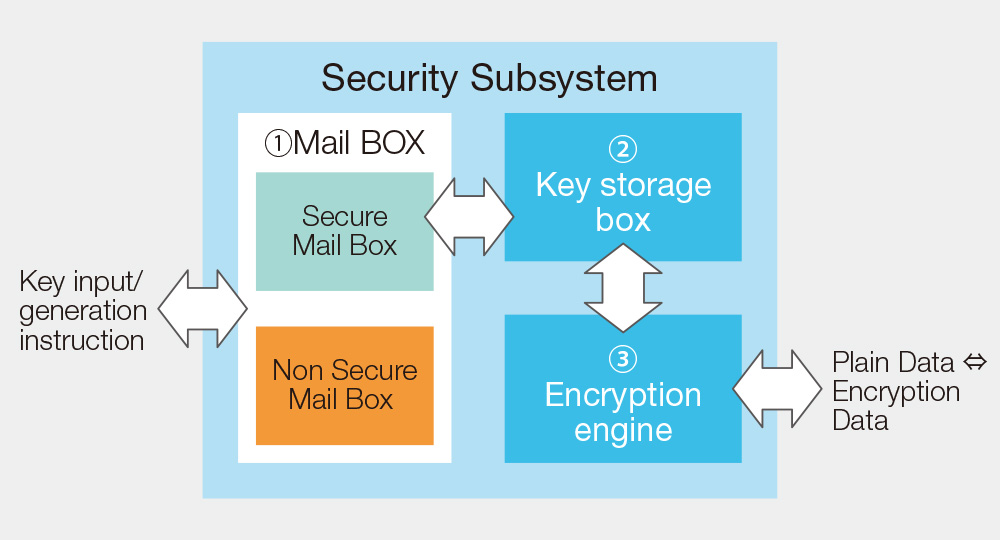
① Secure key generation and input through a dedicated e-mail box
② Secure key storage through locating key storage in a module
③ A dedicated engine that uses a key in a secure key storage box
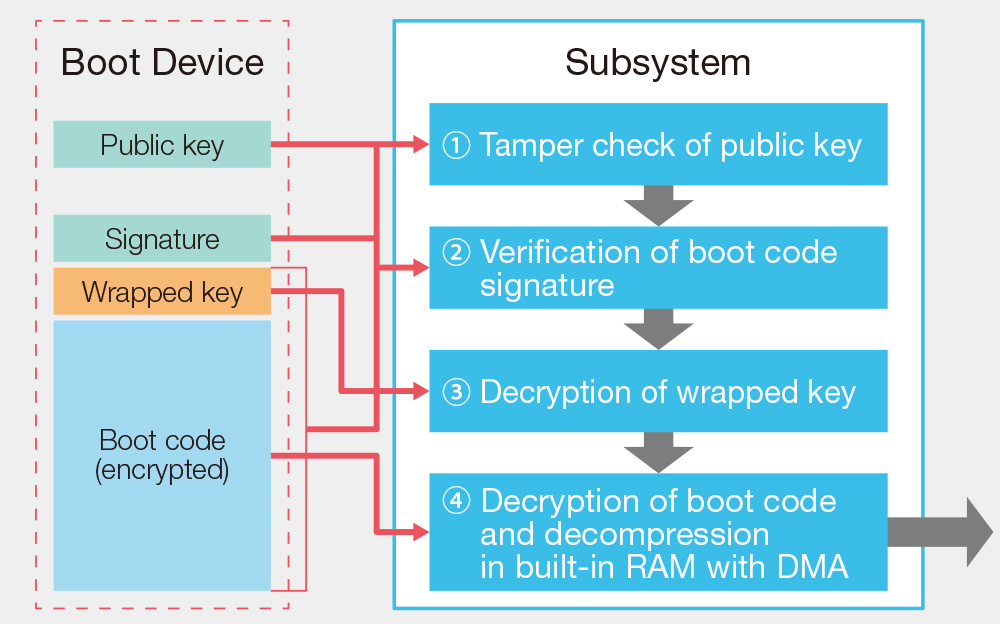
System Configuration
The boot code is executed at the beginning of system startup, and whether a correct program is used or not must be examined on the basis of the boot code. It is the key for a security system where such important code is encrypted and stored, and a mechanism is in place to detect whether such code has been altered. The security subsystem provides a mechanism to protect and securely execute such important code.